Disk Drill is a data recovery tool with only one “forensics” feature so far: it returns the layout information for recovered files in a machine-readable format for further processing (CSV, SQLite database or DFXML). This allows for their forensic analysis for the purposes of identifying, preserving and retrieving sensitive data. DFXML export is available for hard drives, SSD, memory cards and other media storage devices that can be accessed directly. It’s not available for iOS as there’s no direct access to the data storage layer.
To take advantage of this feature, you must have the Enterprise Edition of Disk Drill (or Expert if available at that time). This version can be purchased from the CleverFiles website. If you already have the PRO version, contact us about upgrading to Enterprise.
How to Export Forensic Data
- Launch Disk Drill and perform a scan of the volume in question, as directed in our How to Recover Lost Files with Disk Drill PRO tutorial.
- Once the scan is complete, select File > Export Forensic Data from the top menu bar.
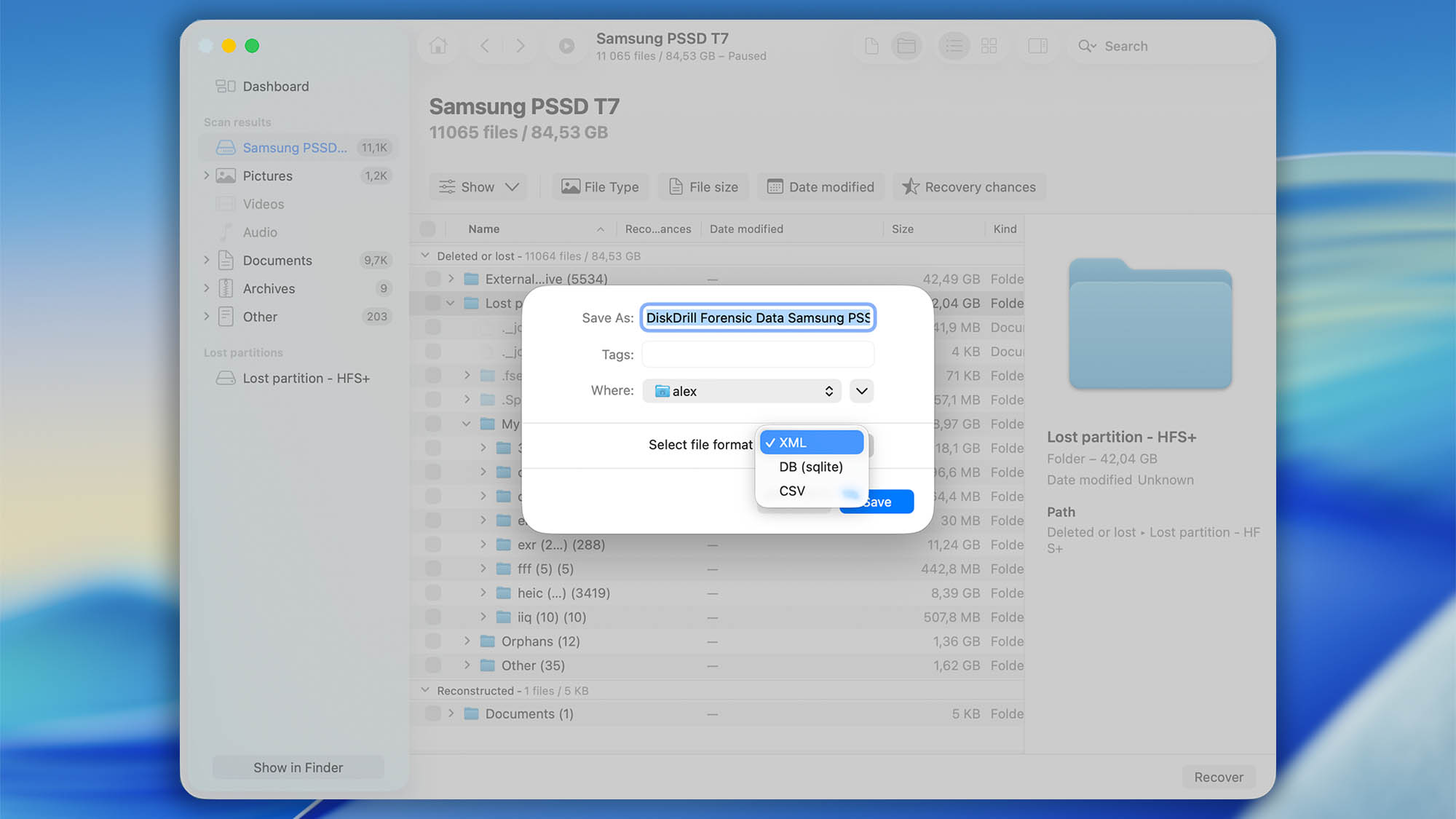
- When the Save window pops up, select the location you wish to save the file to (do not save it to the disk you just scanned or you risk data loss), select the file format (the default is XML, but you also have the option of saving as a DB (sqlite) or CSV format as well), and then click Save.
- You can then import the forensic data file into the program of your choice for further analysis.
Samples
The exported DFXML file (in XML format) will have the following format: XML sample #1, and XML sample #2.
If you choose DB (sqlite) as your export format, the database will consist of two tables, which are the SQL-representations for Digital Forensic XML. The structure of the tables looks like this:
create table fileobject(
fileid integer primary key,
filename text,
family text,
filesize integer,
mtime integer
);
create table run(
fileid integer references fileobject(fileid),
file_offset integer,
img_offset integer,
len integer
);
Here are two samples of the CSV files generated by Disk Drill: CSV sample #1, and CSV sample #2. If you export forensic data into CSV, the data fields will be stored in this sequence:
filename, family, filesize, mtime, file_offset1, img_offset1, len1, …, file_offset8, img_offset8, len8