Viruses and other kinds of malicious programs are responsible for countless data loss horror stories every day, and even tech-savvy users with plenty of experience under their belts are not completely safe from them.
But not all data loss horror stories have bad endings. As long as you know how to recover virus-infected files, you have a fairly good chance of turning the terrible situation around and saving your precious data, and that’s exactly what this article is here to teach you.
Part 1. Not All Viruses Are Created Equal
In this article, we use the term “virus” loosely to encompass a broad range of malicious programs, also referred to as malware.
Instead, let’s focus only on the most important classes of viruses and their potential for causing data loss.
Types of Malware
— CʏʙᴇʀNᴇᴡꜱ (@Cybernews24h) July 6, 2021
#CyberSecurity #DataScience pic.twitter.com/2iWIRZ2h4O pic.twitter.com/Nv6k6V8X7s
File-Infecting Viruses (✅ Recoverable)
Viruses that belong in this class infect mainly executables, such as .exe, .com, etc. Infected executables can make your OS unstable and generate error messages that interrupt your work. In extreme cases, file-infecting viruses can cause the entire storage device to become raw, making it impossible to access any files that were stored on it.
Macro Viruses (✅ Recoverable)
This type of virus is commonly found in Office documents, such as those created using Word or Excel. Many Office documents have built-in support for Visual Basic code, which allows cybercriminals to hide viruses inside them. When the user opens an infected document, they also open the virus hidden inside, allowing it to access other parts of the system.
Web Scripting Viruses (✅ Recoverable)
Web scripting viruses are installed directly from the internet when you visit a malicious website or download an infected file. Such viruses can upload your data to a remote server and then delete it to cause even more damage.
Boot Sector Viruses (✅ Recoverable)
Boot sector viruses are written directly to the boot sector, causing them to be executed each time the infected computer starts. Because this class of viruses often blocks access to the operating system, recovering lost files is slightly more complicated, but not impossible.
Resident Viruses (❓ Potentially Recoverable)
Resident viruses hide in your computer’s memory (RAM), which allows them to easily spread to other parts of your computer and infect all data they come into contact with.
Encrypt Viruses (❓ Potentially Recoverable)
Encrypt viruses include the most talked-about type of malware today: ransomware. The purpose of ransomware is to block access to data by encrypting it using a strong encryption algorithm. The attackers then threaten the victim to make the encrypted data irrecoverable unless a ransom is paid.
Spacefiller Viruses (❌ Irrecoverable)
This rather rare class of viruses is characterized by its insatiable hunger for empty disk space. When a spacefiller virus encounters any disk space that hasn’t yet been filled, it quietly installs itself there, making detection difficult.
Overwrite Viruses (❌ Irrecoverable)
As their name suggests, overwrite viruses aim to cause damage by overwriting system files and user data. One commonly encountered overwrite virus is called LoveLetter. This dangerous virus has the ability to act as a trojan and an email worm, which allows it to spread quickly and across multiple networks.
Part 2. How to Recover Virus Infected Files?
As we’ve explained in the first part of this article, not all viruses are created equal, so you can’t expect a single recovery strategy to address all cases of virus infection that you may possibly encounter.
In this part, we describe several common virus infection scenarios and provide detailed step-by-step instructions to explain how you can recover from them.
Recover Hidden Files from a Virus Infected USB Flash Drive

Because USB flash drives are primarily used to transfer files between different computers, they often become infected with viruses, trojans, and other malware.
If you’re suddenly missing files that were stored on your USB flash drive, the chances are that they’ve been hidden by one of the viruses described above. The good news is that unhiding them may still be possible, as long as you act quickly and follow our instructions.
Reset all file attributes to unhide files hidden by a virus:
- Press Win + X and select Windows PowerShell (Admin).
- Navigate to the infected USB flash drive using the cd command.
- Enter: attrib -h -r -s /s /d X:\*.* (replace X with your drive letter)
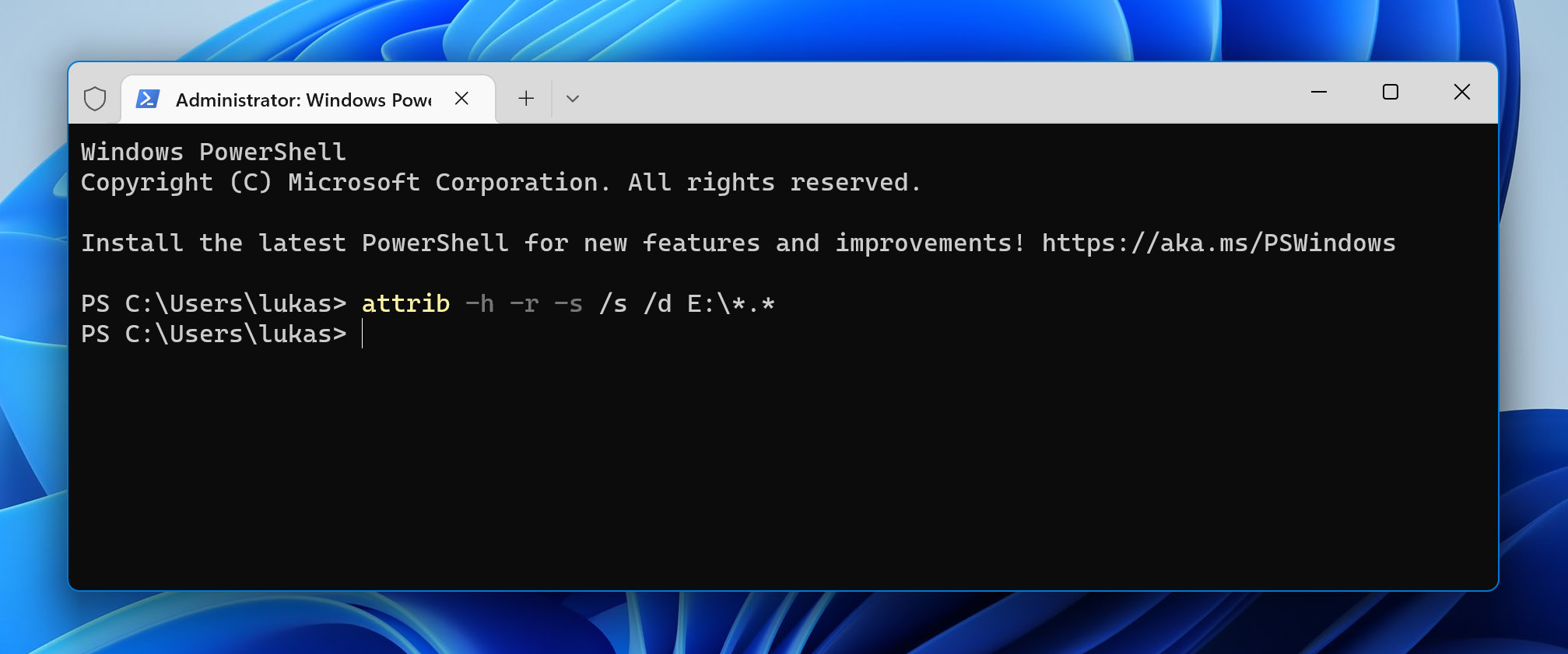
If you’re lucky, then this is all you need to do to regain access to your hidden files. The same instructions can also help you get rid of the so-called Recycler virus, a commonly encountered variation of the W32.Lecna.H worm.
Safely Recover Files from an EXE Virus

EXE viruses are the most common type of file-infecting viruses. They can be encountered on malicious websites, found bundled with shady software, or disguised as legitimate files on file-sharing websites.
Just like all other file-infecting viruses, EXE viruses can disable parts of the operating system, hide important files, or even cause widespread data corruption. While files that are hidden by a Trojan can usually be recovered with nothing but the attrib command (see the previous method), proper data recovery software is typically needed to recover from an EXE virus.
Step 1: Install data recovery software
There are many data recovery software solutions that can help you safely recover files from an EXE virus, but we recommend Disk Drill.
Why? Because Disk Drill is easy to use yet powerful enough to recover over 400 file formats from all commonly used Windows, macOS, and Linux file systems. Best of all, you can use it to preview an unlimited number of files to verify their recoverability before paying any money to get them back.
Just make sure to install Disk Drill on a different storage device than the one you want to recover to avoid overwriting the very same data you’re trying to save.
Step 2: Scan the infected drive
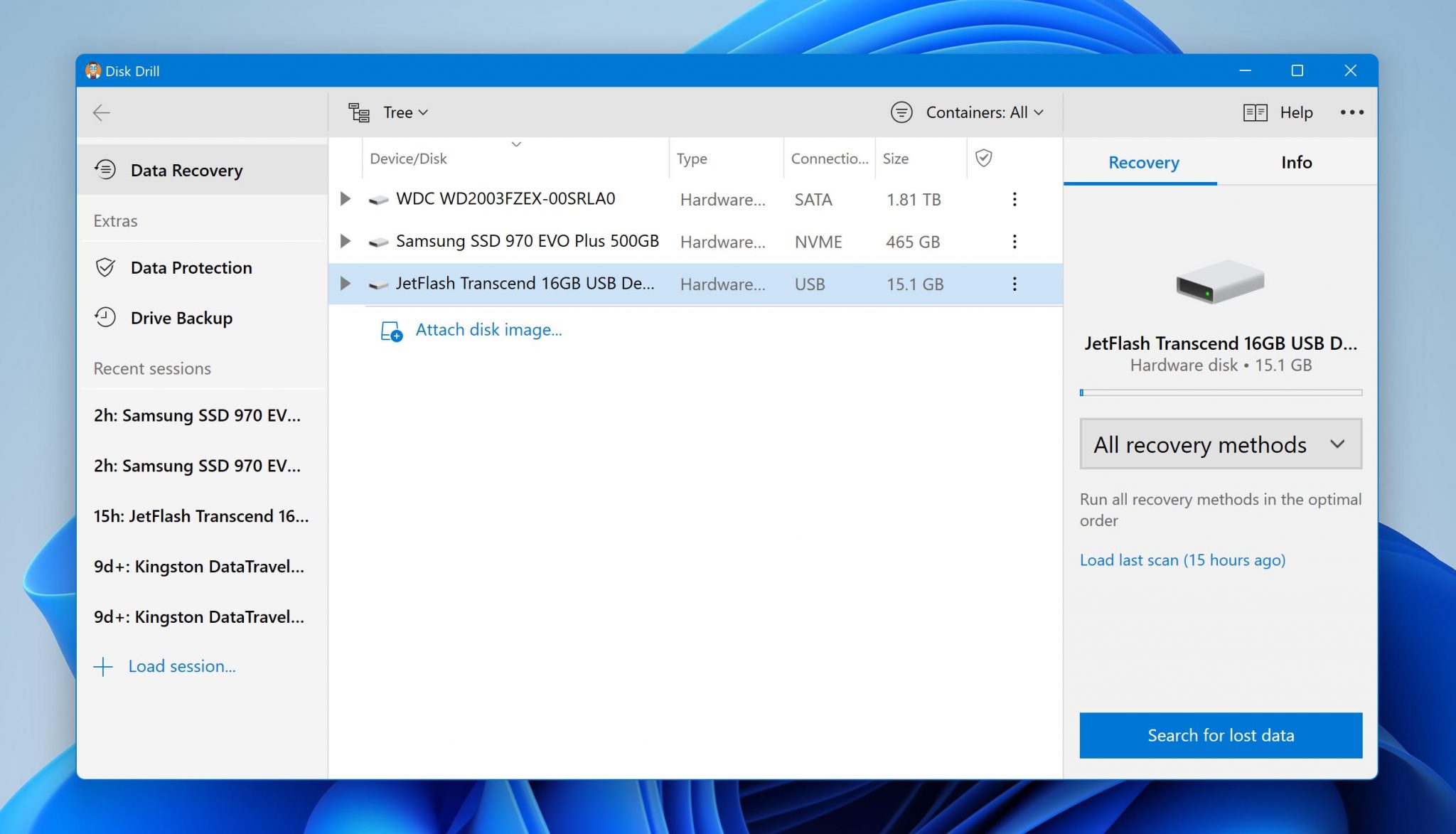
Assuming you’ve picked Disk Drill as your data recovery software of choice, all you need to scan the infected drive is select it and click the Search for lost data button. Disk Drill will automatically run all recovery algorithms in the optimal order.
Step 3: Select files for recovery
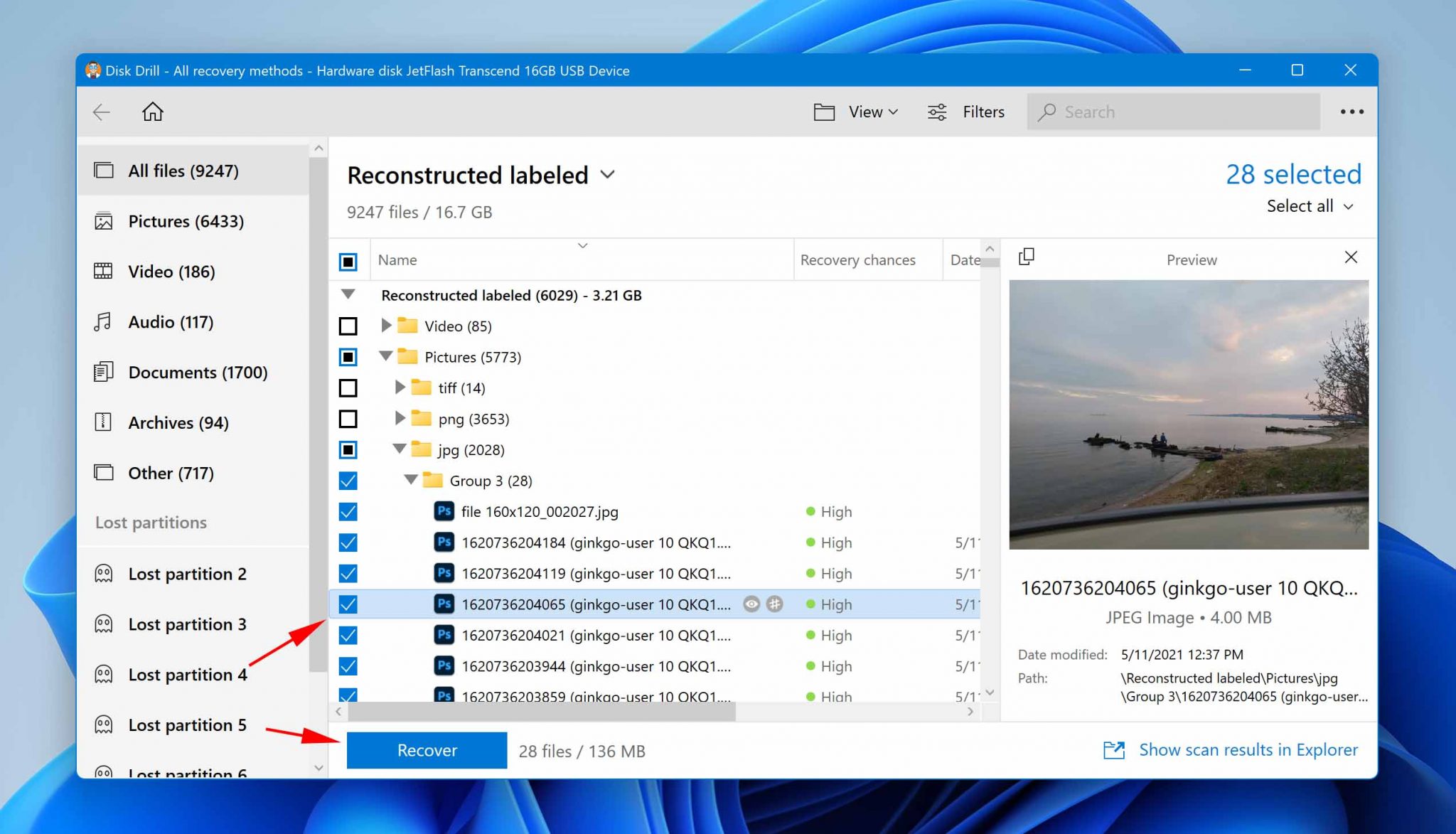
Depending on the size of your storage device, it might take Disk Drill a short while to finish scanning for lost data, so be patient and let it do its job. Once the scan is over, you can preview all recoverable files and select those you want to get back.
Use Disk Drill’s handy search results filters to easily locate the data you want to recover while hiding everything else.
Step 4: Recover selected files to a safe location
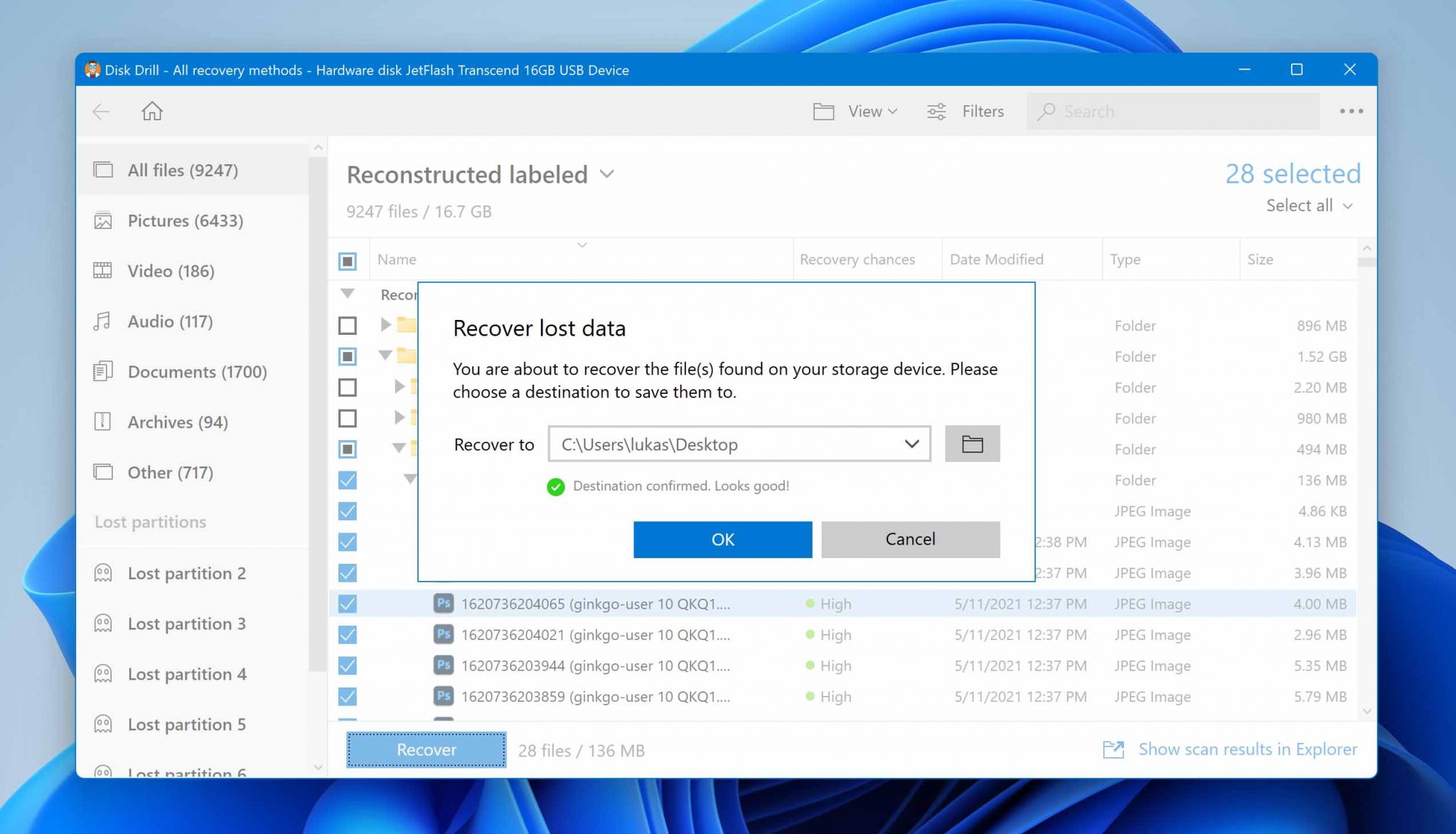
Next, click the Recover button to recover the selected files. Disk Drill will ask you to specify the recovery directory, and you should select a folder that’s located on a different storage device than the one you’re recovering from. Again, this is to avoid overwriting the same files you’re trying to recover.
Step 5: Format the infected drive
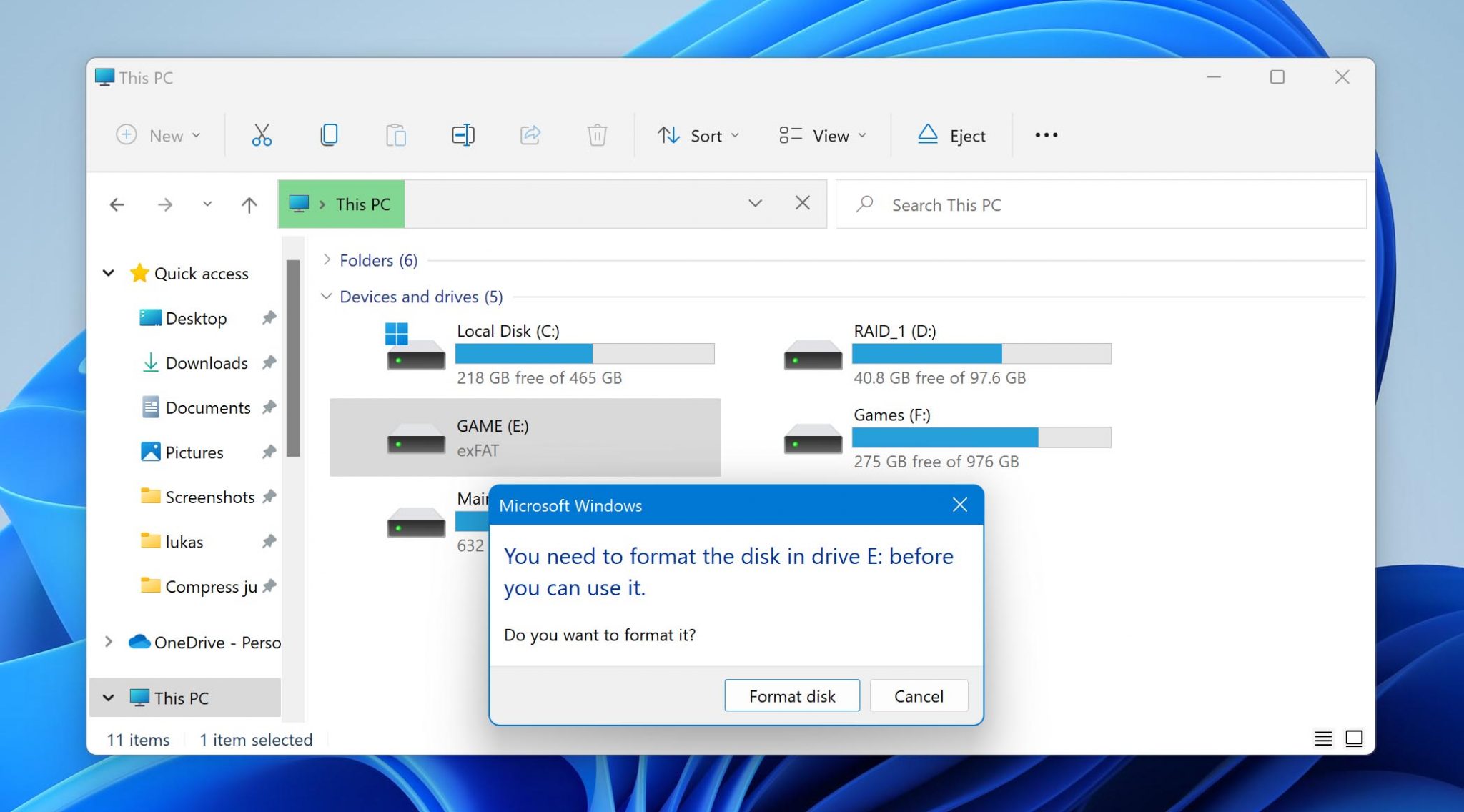
Finally, you should format the infected drive to prevent the spread of the virus. We recommend you complete this step even if you’ve already deleted the virus using an anti-malware solution like Microsoft Defender because you don’t want to take any chances when it comes to viruses.
What is a Ransomware Attack?
Ransome is malware (malicious software) that blocks access to the victim’s computer system or encrypts its data. In such cases, the attacker demands a ransom fee in exchange for returning access to these files, databases, etc. Mostly, these ransom demands are accompanied by a deadline. If the victim doesn’t meet these demands, they risk losing data forever.
Encryptors encrypt your important data like documents, pictures, media, etc., and you would require a decryption key to access it. On the other hand, the Screen Locker malware interferes with basic computer systems with a “lock” screen that demands a ransom. However, it’s evident that these types of malware are designed to extort money from people.

While ransomware initially targeted individuals and personal computers, attackers have increasingly begun to attack businesses and organizations. Some examples of major ransomware attacks are the WannaCry malware that infected over 250,000 systems worldwide, the Bad Rabbit ransomware that affected media companies across Russia and Ukraine, and CryptoLocker, among others.
Ransomware often targets people or companies through phishing emails, software vulnerabilities, etc. If you suspect that you’ve been attacked by such malware, it’s important to act quickly before it gets to your critical files or data. You can follow these steps when responding to such attacks:
- 🔌Isolate the impacted device – If any ransomware has attacked your system, the first response should be to disconnect connected devices, the internet, etc., to minimize damage and ensure that your network remains safe. You might even want to power down your device, if necessary.
- 🔎Identify the Ransomware – It’s also important to try and identify the type of malware you’re dealing with. There are various tools available to help you through the situation. You can even use No More Ransom, an initiative by McAfee to help decrypt your data.
- 🕵️Consult a Professional – Another way to deal with ransomware attacks is to immediately consult a professional who can help you find the roots of the vulnerability and even identify all impacted systems. This information can help them eradicate the threat for good.
- 💾Restoring systems through backups – If you’ve created backups of your files and systems, you’ll be able to restore them quickly. Just make sure you scan the system through your antivirus to get rid of any lingering threats and get back to work efficiently.
Recover Ransomware Infected Files
There’s a good reason why ransomware attacks have been making the headlines for years now: they’re extremely difficult to recover from. There were many high-profile instances where infected individuals and organizations alike decided to pay a hefty ransom just to regain access to their lost files.
But paying a ransom doesn’t guarantee you or your organization will get any data back, as explained by the FBI. Unsurprisingly then, the FBI doesn’t support paying a ransom in response to a ransomware attack. Instead, you should attempt to decrypt your files and, if that fails, recover them from a backup.
Option 1: Decrypt files encrypted by ransomware:
- Remove the ransomware using a reputable anti-malware solution, such as Windows Defender and its Offline scan option.
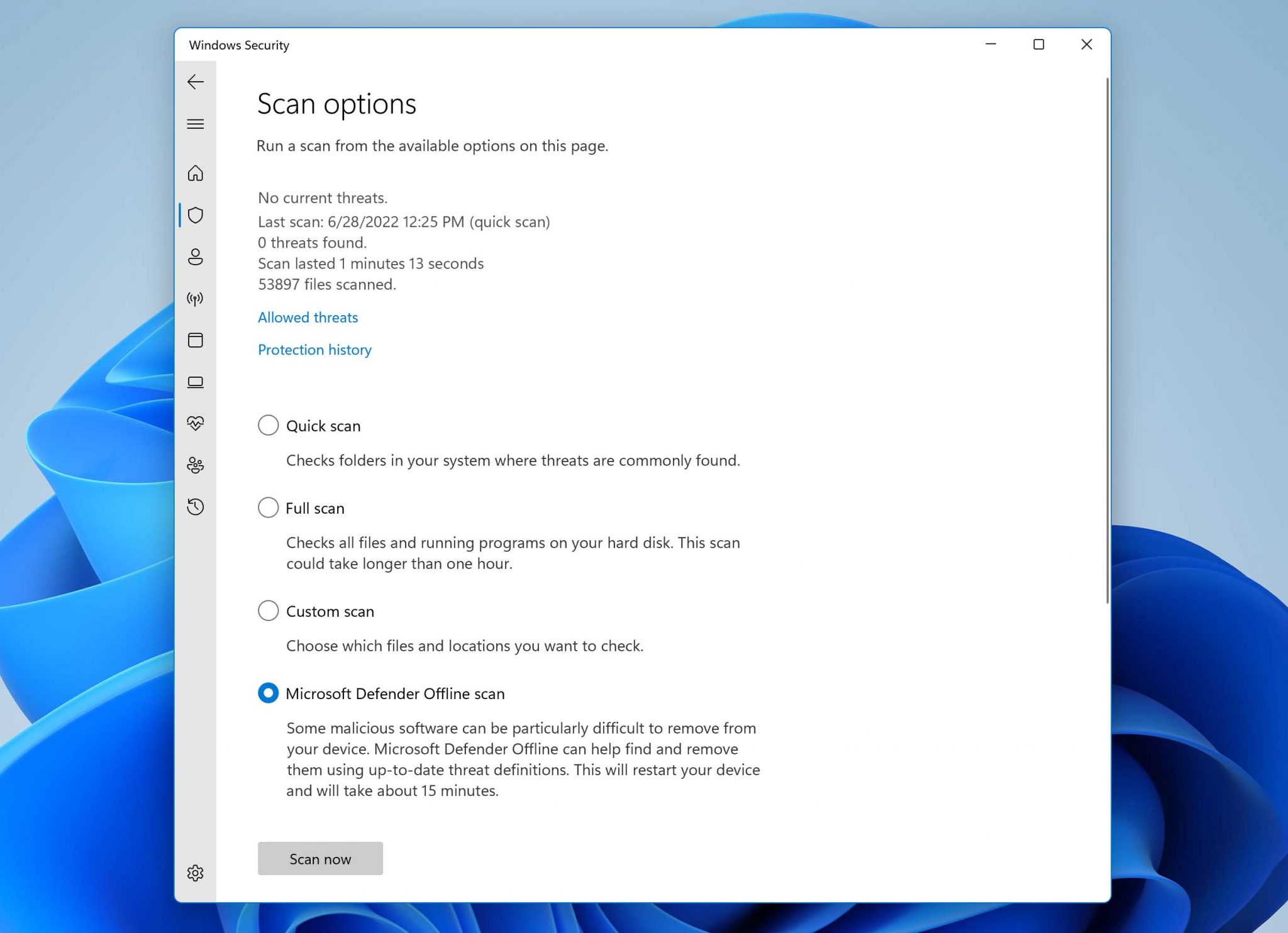
- Find the latest decryptor for the ransomware.
- Download and launch the decryptor.
- Use the decryptor to scan the encrypted storage device.
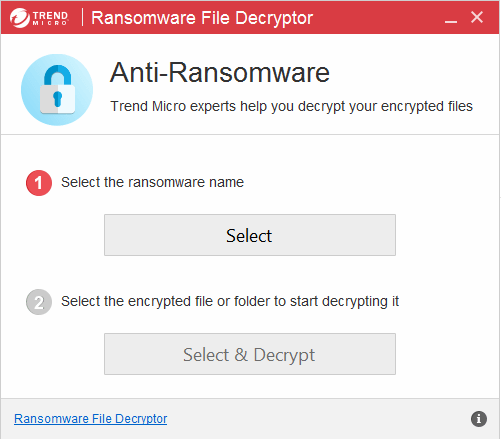
- Wait for your files to be decrypted.
If you’re attempting to recover ransomware infected files from a system drive, then we recommend you disconnect it and decrypt it as a secondary drive from a clean computer.
Option 2: Recover ransomware infected files from a backup:
![]() Are you unable to find a suitable decryptor for the specific strain of ransomware that has encrypted your files? In that case, your only salvation is an existing backup (local or cloud).
Are you unable to find a suitable decryptor for the specific strain of ransomware that has encrypted your files? In that case, your only salvation is an existing backup (local or cloud).
Before you recover lost files from a backup, make sure that the ransomware responsible for their loss has been completely removed from your system. It’s a good practice to format all potentially infected storage devices and reinstall the operating system after every infection.
The actual steps you need to take to recover your data depend entirely on your data backup method of choice. When recovering from a local backup, you can simply drag & drop your files. On the other hand, most cloud backup solutions come with a backup tool to help you synchronize local and remote files.
Part 3. How to Prevent Files From Being Infected by Virus?
If your operation system has fallen under attack due to malicious elements, it can often compromise your networks and important data. This, in turn, can have far-reaching, negative consequences for your company or organization.
However, there are some best-practices you can follow to prevent such a situation. These are:
- 🌐Cyber Awareness – The most popular way for cybercriminals to attack unassuming victims is through phishing emails, malicious attachments, etc. that are then used to compromise your data or attack organizations by gaining access to their records. To prevent such a situation, employees and individuals need to learn to verify unknown software, scan suspicious attachments, avoid sharing personal information over the internet, etc.
- 📀Create Backups – Virus attacks can often make your data inaccessible, delete it, or encrypt your data to extort you for monetary gains in cases of ransomware attacks. A robust data backup solution would offer you additional protection that would come in handy if your system was under attack. If you regularly backup your data, the data lost due to a virus infection would be negligible.
- 💻Keep the computer up-to-date – One of the basic ways to protect your system against virus attacks is to ensure that all your software remains up-to-date. This is important because your software updates contain features that can withstand the latest security threats. Thus, keeping your computers updated and applying security patches that help vulnerability to virus attacks.
- 🔒User Authentication – The first line of defense against malware is to maintain strong user authentication since cybercriminals often gain access to systems through stolen login credentials. Having a strong password policy in place, establishing multi-factor authentication, etc., can help avoid dangerous virus attacks.
- 🔧Reliable Antivirus tools – Anti-virus software routinely scans your emails, files etc., for viruses trying to invade your operating system. It can identify and eradicate any threats that might attempt to invade your system. There are several efficient anti-virus tools available on the market and you can choose the software package that matches your requirements.
- 🧱Use your Firewall – Your network firewall is like a protective boundary around your computer that blocks unauthorized access to it. When you’re configuring your computer, ensure that you activate the in-built firewall that your system provides. You even have the option to adjust firewall settings based on your preferences and requirements.
Conclusion
There are countless different types of viruses, some more dangerous than others. In this article, we described several recovery methods to help you regain access to files that have been hidden, deleted, and encrypted. Hopefully, this will be your last encounter with a virus—or at least virus-caused data loss.
FAQ
You can follow these general steps to fix most infected files you come across:
- Determine which kind of infection you’re dealing with using an online virus scanner tool like VirusTotal.
- Look for instructions on how to fix the infection.
- Follow the instructions to remove the infection from the file.
Assuming you’ve already used anti-malware software like Windows Defender to remove the source of the infection, you can now scan the virus-infected USB using a data recovery tool like Disk Drill to recover missing files:
- Launch Disk Drill and select the infected USB.
- Click the Search for lost data button.
- Wait until all recoverable files are discovered.
- Select the files you want to recover.
- Click the Recover button.
There are many different Trojans that can infect your files, but you can deal with most of them by following the same steps:
- Disconnect your computer from the internet.
- Scan it using anti-malware software.
- (Optional) Reinstall your operating system and format your drives.
- Restore lost files from a backup or using data recovery software.
To remove a virus from an external hard drive without losing data, you need to avoid formatting and follow the instructions below instead:
- Install reliable anti-malware software on an isolated computer.
- Connect the external hard drive to the computer.
- Scan it using the installed anti-malware software application.
Yes, there are some cases in which your can recover ransomware infected files without having to pay the ransom to the attacker. Some of these methods are:
- Use decryption tools to recover files encrypted by ransomware.
- Attempt to recover ransomware infected files using a backup.
- Recover files using data recovery software like Disk Drill.
- Use the System Restore setting on your Windows operating system.
You can attempt to decrypt your files if they’ve been infected by ransomware. While it might not work in some cases, you might be able to recover your encrypted files.
The steps to decrypt your files are:
- Remove the ransomware using a trusted anti-malware software like Windows Defender.
- Find the latest decryptor for the ransomware that has affected your system.
- Download and Launch the decryptor.
- Let the decryptor scan the affected storage device and then wait for your files to be decrypted.
If you use a Windows operating system, you can attempt to restore your files using the ‘System Restore’ utility. Since this tool stores backups of your Windows device, you would be able to recover versions of the file that haven’t been encrypted by the ransomware.
Follow these steps to use the System Restore option:
- Navigate to the Control Panel.
- Now, select the System and Security option.
- Choose Backup and Restore, and click Restore Files from Backup to complete the process.
If your computer system gets infected by ransomware, it’ll most likely block your access to system files by encrypting them. The attacker offers you access to a decryption key only in exchange for a ransom. However, this entire process is unreliable and you can’t be sure if access would be returned or your system would be secure after paying the ransom.
In such a situation, you can turn to file backups or decryption tools to attempt and recover your files without engaging with any ransom demands.

