Disk Drill can’t perform Quick Scan, Deep Scan, or Catalog Rebuild on iPhones/iPads because iOS never exposes its raw disk to apps or computers and all user data is hardware‑encrypted. Instead, Disk Drill performs logical iOS recovery by analyzing a local device backup (it can create a temporary backup for analysis) and reconstructing supported artifacts (e.g., contacts, chats, photos). On iOS 13+, some items—like call history—require an encrypted local backup to appear.
The iOS Security Model That Blocks Quick/Deep Scanning
iPhones and iPads use APFS plus Data Protection classes, with per‑file encryption keys stored in keybags tied to the device’s hardware. While the device is mounted and after the user authenticates, iOS manages when specific file classes can be accessed; it never exposes the underlying blocks for external scanning. Even if you could read raw sectors, you’d mostly see ciphertext. That’s by design.
Apple also restricts host‑computer access to the device to backup/management protocols (Finder on macOS, Apple Devices app/iTunes on Windows), not to the storage volume itself. That’s why traditional file‑system scans aren’t an option.
So… Why Are Quick and Deep Scan Missing on iOS?
- No block device: iOS doesn’t present a raw volume to scan; it exposes only backup interfaces. Deep/Quick scans need block‑level or file‑system‑level access.
- Strong encryption at rest: Without the device’s hardware‑bound keys and authentication state, sector data is unreadable ciphertext, so signature carving won’t yield usable files.
- Different data source: iOS recovery is backup‑centric, not disk‑centric, so Disk Drill reads structured databases rather than free space. Hence the different grouping and limited artifact set.
What Data Types Can Disk Drill Usually Recover From iOS?
Disk Drill targets specific, high‑value categories commonly stored in backups—such as Contacts, Chats, Photos, etc.—and displays them by type. Availability depends on the iOS version, whether the backup is encrypted, and what the user originally backed up.
🤔 Why encrypt iOS backups to recover the most data?
Starting with iOS 13, Apple restricts several sensitive data types to encrypted backups only. If a local backup isn’t encrypted, recovery tools can’t acquire or parse key items like Call History, Safari Browsing History, and Safari Open Tabs. Encrypted backups also include data that unencrypted ones omit—such as saved passwords (Keychain), Wi‑Fi settings, website history, Health data, and call history—which are often essential for a complete recovery. (Face ID, Touch ID, and your device passcode are not included in any backup.)
To recover the fullest set of iPhone/iPad data—including call logs and Safari data—you need an encrypted backup. Use a strong password you can remember.
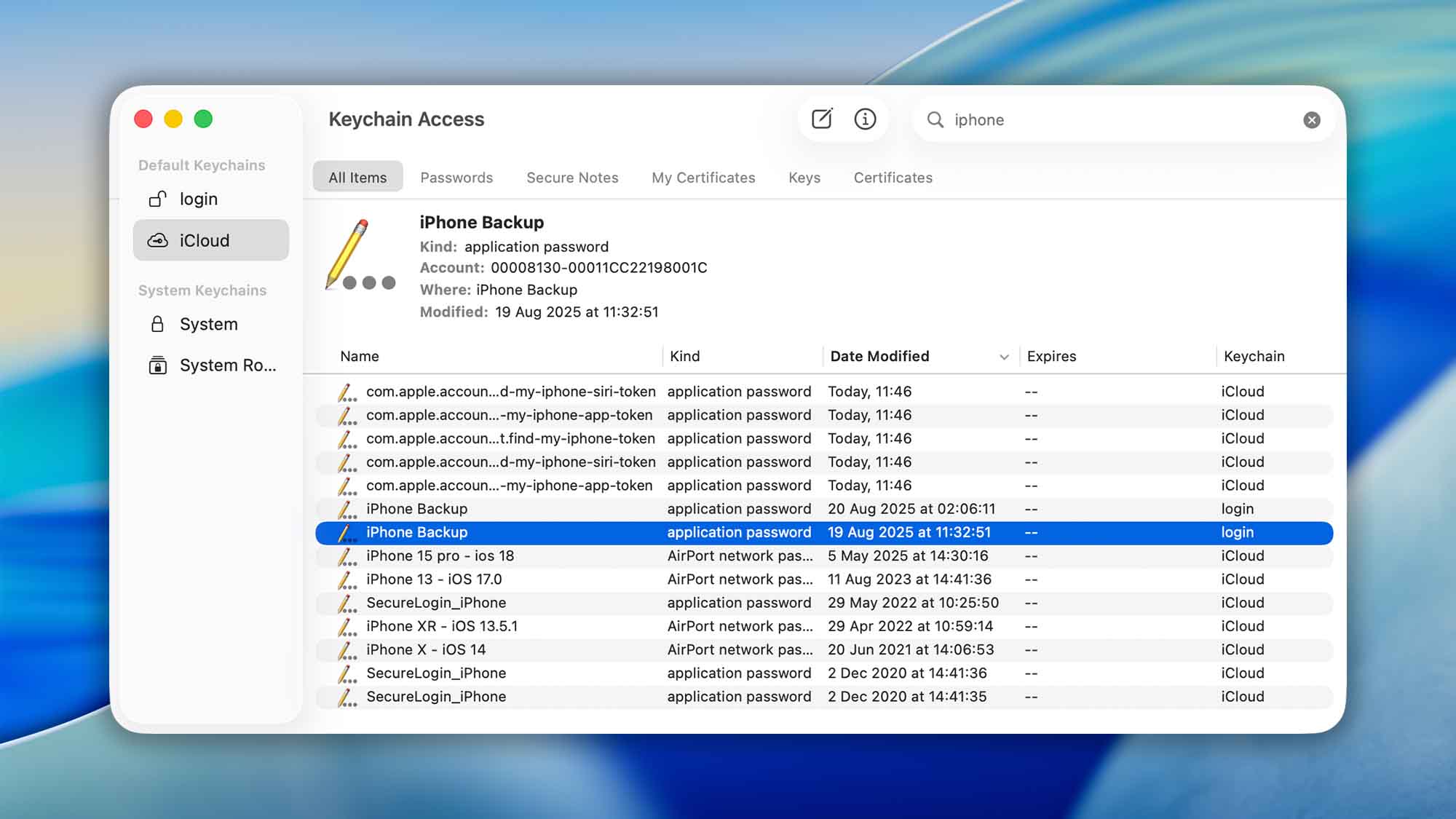
How to find your iPhone/iPad backup password (Keychain Access)
- Open Keychain Access. Go to Applications → Utilities → Keychain Access (or press Command–Space and search for Keychain Access).
- Search for “iPhone Backup”. In the upper‑right search field, type iPhone Backup. (On some Macs you might see items like iOS Backup or similar—open the one that matches your device/most recent date.)
- Open the item and show the password. Double‑click the iPhone Backup entry to open it. In the Attributes tab, check Show password.
- Authenticate. Enter the password for your login keychain (the same password you use to sign in to your Mac). If prompted, you can use Touch ID.
- Copy your backup password. The field will reveal your encrypted backup password. Copy it and use it to unlock the backup in Finder/iTunes or your recovery tool.
If you don’t see “iPhone Backup” in Keychain
- The encrypted backup may have been created on another Mac or under a different macOS user account.
- The password wasn’t saved to Keychain when encryption was enabled.
Why Disk Drill’s iOS Results Look Different From Desktop Scans

Desktop scans mirror your file system (folders, filenames). iOS recovery is artifact‑centric because it’s rebuilt from backup databases (message threads, address book entries, photo libraries). You’ll see categories like Chats and Images instead of the original folder trees from the device. That’s expected behavior for logical iOS acquisition.
Phone storage is often larger than the free space on your computer. To complete a data‑recovery scan in Disk Drill, plan for at least 2× the amount of data currently stored on the phone. If your Workspace Folder is on the system drive, add an extra 5 GB of free space.
Example: If your phone has 100 GB in use, ensure 205 GB free on the system drive. If you set the Workspace Folder to an external/non‑system drive, 200 GB free on that drive is sufficient.