In an era dominated by digital data, the menace of cyberattacks looms large. Every click, every download, every online interaction can be a potential gateway for hackers. Here, we arm you with top-notch strategies to fortify your digital fortress, ensuring your personal and professional data remains protected.

In the midst of global challenges, computer systems worldwide are facing a surge in cyberattacks. Malicious hackers, with no regard for ethics, are exploiting the public’s vulnerability, launching sophisticated attacks. These black-hat hackers, known for their lack of moral compass, are seizing opportunities to infiltrate, disrupt, and compromise digital security, marking a disturbing escalation in cyber warfare.
In this article, we will look at some of the targeted attacks that have emerged in the hopes that you can use this information to strengthen your data protection policies to thwart cybercriminals. We will also talk about a software tool that can be used to recover from data loss if your system is struck by one of these malevolent attacks.
The Rising Incidence of Cyber Attacks
Threats to the healthcare sector as well as average citizens are on the rise in the wake of the global pandemic. Important health-related agencies like the U.S. Department of Health and Human Services (HHS) and the World Health Organization (WHO) have been repeatedly targeted by hackers.
Fortunately, so far the attacks on these organizations have been unsuccessful. In other cases, a hacker attack has resulted in significant damage to the healthcare infrastructure. In Illinois, the Champaign-Urbana Public Health District’s website was down for several days as they recovered from a ransomware attack.
According to researchers at SonicWall, new and pointedly destructive malware has recently been identified that employs a pandemic-theme to trick users. It is designed to cause destruction rather than attempting to obtain financial gain from their victims. Two of the identified malware variants rewrote a computer’s master boot record (MBR), essentially destroying the machine. Another variant posed as a pandemic ransomware attack but in truth was designed to steal passwords before rewriting the MBR.
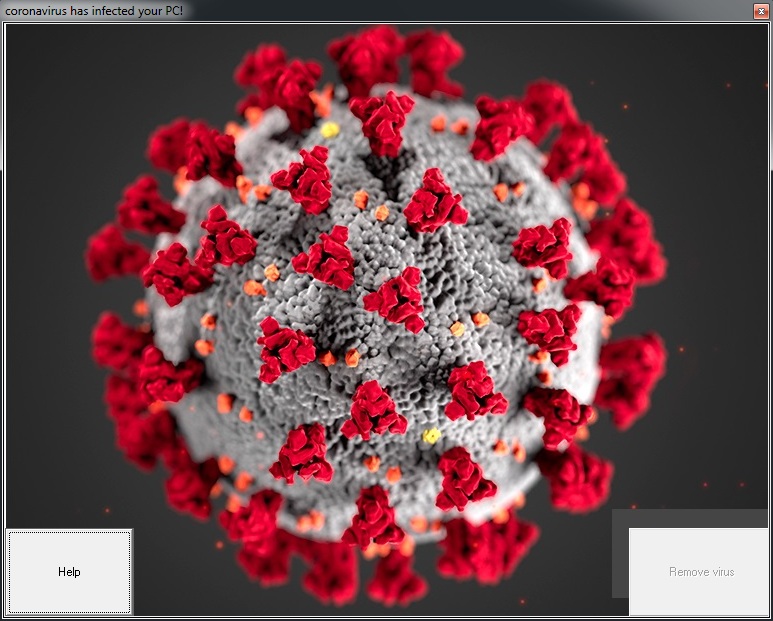
Security researchers have identified a 667% increase in the number of pandemic related spear-phishing attacks. Over 9,000 phishing initiatives were detected and have been steadily on the rise as the pandemic spreads. The goals of the attacks range from malware distribution to ransomware and credential theft. One particularly wicked blackmail attack threatens to infect an individual and their family with the coronavirus unless they pay a ransom.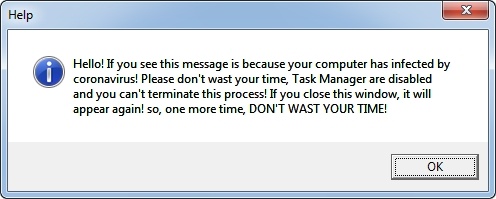
Google says they saw 18 million daily malware and phishing emails related to the pandemic in the past week.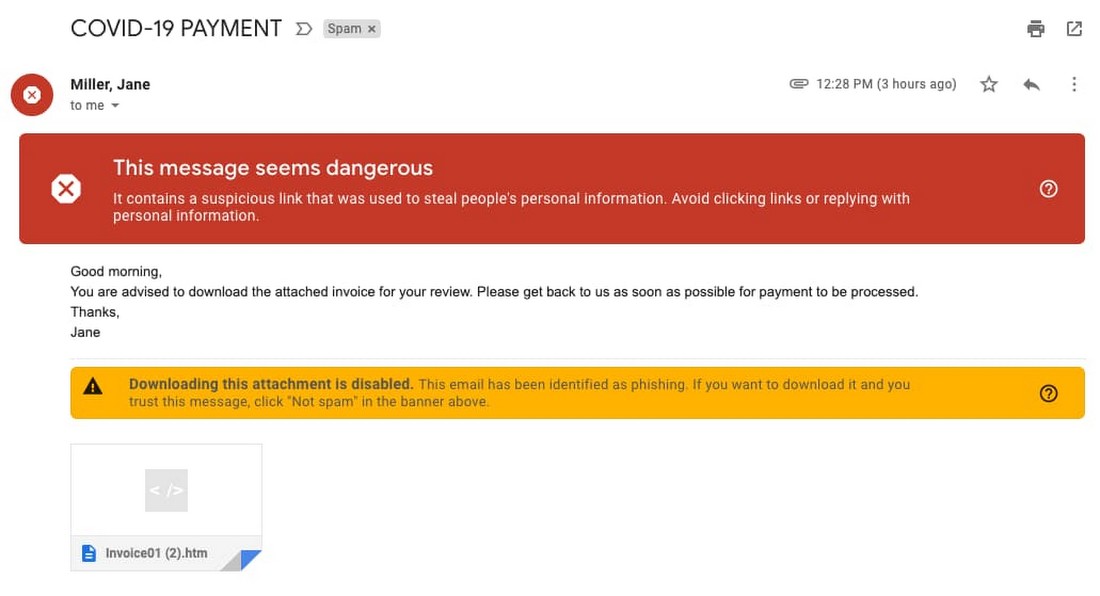
These are just a few examples of the threats to computer systems and their data being perpetrated by criminals using the fear of pandemic to further their aims. Unfortunately, this adds more stress to that already being experienced by society. These cybercriminals are demonstrating that they are bottom-feeders with no semblance of a conscience. Computer users need to take every precaution possible to protect their data resources.
Protecting your Data Resources
Several techniques should be used in combination to protect your computer systems from being impacted:
1. Choose the Right Antivirus Protection.
Virus-scanning software is an essential first wave of defense that should be installed on all computer systems. Choose a reputable solution and make sure you keep its databases updated to address newly discovered threats. Take reports generated from the anti-virus tool seriously and remove any suspicious software from your computer as soon as possible.
2. Secure a Computer Network.
Password protect networks and network components to minimize the chances of unauthorized access to your systems. Non-trivial passwords should be required for network access. The same can be said for routers and other devices used to provide the network infrastructure. Many devices are installed with default credentials which is like leaving the door wide open and inviting an attack. Change these immediately to raise your level of protection.
3. Watch out for phishing emails.
Think twice before clicking on links in emails and instant messages. After thinking twice, take a deep breath and think again. Scammers are using fear and misinformation in attempts to lure users to fall victim to phishing attacks. This is a terrible tactic that can only be defeated by individual vigilance. Clicking an infected link can result in delivering malware directly to your machine. In corporate settings, a single wrong click can inadvertently affect the entire enterprise.
4. Backup your Data.
Data backups are a valuable commodity that should be a regular part of your computer maintenance regimen. The importance of backups is often overlooked until disaster strikes and systems need to be rebuilt. Make sure that you have a viable backup strategy in place and keep the storage media in a safe place. When all else fails, they provide the raw material required to recover your important data.
Recovering from a Hacker Attack
If you are hit by a destructive computer virus or malware attack you may need to perform data recovery to save your important information. Disk Drill is a software solution that can be instrumental in getting your data back and offers additional protection capabilities to keep it safe in the first place. The software offers users a simple and effective way to recover from a variety of data loss scenarios including the damage caused by a cyber attack.

Systems that are infected with malware or a virus may be subjected to random data deletion, leaving users scrambling for a solution. Data recovery software can help Windows and Mac users scan their systems for deleted data and recover it safely. The tool recognizes over 400 filetypes and supports virtually any type of disk-based storage device. Its advanced scanning algorithms will examine the storage media on a sector-by-sector basis and reconstruct files that appeared to be lost forever.
Disk Drill’s main functionality is in data recovery, but the application also offers data protection features that can be used to safeguard your valuable information. The tool lets you create a byte-level backup of your disks which can be used to recover your files when necessary. This type of backup includes deleted data which makes it possible to perform recovery on files that had been lost before the backup’s creation.