Malware and viruses present some of the most challenging issues facing computer security experts. As more and more of the world’s commerce and industrial control is performed using computers, the threat of system infection and its repercussions have grown exponentially. The emergence of ransomware that threatens to delete a computer’s data if the demands of the attackers are not met is one variant which can lead to serious financial losses impacting the affected users.
Malware and viruses present some of the most challenging issues facing computer security experts. As more and more of the world’s commerce and industrial control is performed using computers, the threat of system infection and its repercussions have grown exponentially. The emergence of ransomware that threatens to delete a computer’s data if the demands of the attackers are not met is one variant which can lead to serious financial losses impacting the affected users.
Other viruses are designed simply to perform destructive acts on the machines that they infect. There is no ransom requested which might save the data on the infected machine. The goal of this type of attack is to destroy the functionality of the targeted machines.
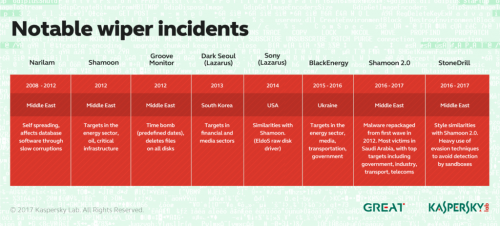
One of the most pernicious viruses currently causing mayhem and destruction is known as Shamoon. It attacks computers that are running the Microsoft Windows operating system. Let’s take a close look at this potentially devastating weapon in the arsenal of cyber-warriors.
What is Shamoon and How Does it Work?
Shamoon, also known as W32.Distrack, is an aggressive, disk-wiping malware program that was first seen in attacks on the Saudi energy sector in 2012. The discovery of the malware was announced by Symantec, Seculert, and Kaspersky Labs in August of 2012. In the 2012 attacks, computers infected with the malware had their master boot records wiped and replaced with an image of a burning U.S. flag. Variants of Shamoon use other images when overwriting a computer’s files.
There is no ransom requested by Shamoon and it is an example of weaponized malware that is designed for use in cyber-warfare. It uses a combination of a number of components to infect computers. They are:
- The Dropper — This is the first component and is used to create a persistent service on the infected computer named NtsSrv. It comes in 32 and 64-bit versions and drops its payload based on the architecture it discovers. It copies itself to other network attached computers to spread its malicious code.
- The Wiper — Shamoon’s next component is the wiper, which is used to drop a third component. This is the Eldos driver and is used to overwrite the hard disk’s master boot record (MBR) with the current image embedded in the malware. The driver enables user-mode access to the hard disk without using the Window APIs. After the MBR is overwritten, the system is unusable.
- The Reporter — This final component establishes communication with a command and control server. The attackers operate this server and can use it to download additional code, change the pre-configured disk-wiping time, and send reports to verify that a particular disk has been destroyed.
Who is Behind Shamoon?
The destructive nature and precisely chosen targets of the current Shamoon infestations indicate that it is the work of a coordinated team of hackers. According to infoworld.com, security experts at McAfee believe that the original group behind the malware has been replaced by the cyber-warfare capabilities of a rogue nation-state. Though the company does not explicitly name the culprit, evidence points to Iranian hacker groups that may be associated with its government.
The First Wave of Shamoon Attacks
When it first reared its ugly head, Shamoon was found to be infecting the computers of the Saudi Arabian oil company Saudi Aramco. According to cnet.com, more than 30,000 workstations at the company were affected by the malware. A group calling itself the Cutting Sword of Justice claimed responsibility for the attack.
Their justification for targeting the energy company was the close relationship it has with the Saudi government. The rationale for the attack was in retribution for supposed crimes that the Saudis had perpetrated on the neighboring countries in the region such as Syria and Lebanon. Suspicion fell on the Iranian government as retaliation for Saudi Aramco’s commitment to produce more oil to keep up supplies during a U.S.-European Union embargo against Iran.
This attack is considered the first substantial use of malware to conduct an attack. Previous hacktivist initiatives were usually carried out through distributed denial of service (DDoS) attacks. Though no conclusive link could be proved, days after the Shamoon attack, sensitive details including admin passwords pertaining to Saudi Aramco’s chief executive were posted on Pastebin. This could be a coincidence or the result of the reporting component of Shamoon copying important details to the Internet before proceeding with the disk-wiping procedure.
Recent Events Involving Shamoon
Shamoon resurfaced in 2016 in a new version that also focused on Saudi targets. It was set to begin destroying disks on Thursday evening, which coincides with the end of the Saudi workweek in order to enact the maximum damage before being discovered. The malware was also configured with stolen passwords from the targeted organizations. Some serious planning went into launching this attack, which points to a well-organized group driving the action.
The malware seemingly disappeared after its 2016 attacks, only to emerge again in late 2018. It appears that the code is being reused periodically after undergoing modifications that make it even more destructive. According to symantec.com, the latest incarnation of this malware features a new wiper that deletes files from the infected computers before wiping the master boot record.
The new wiper makes recovery of the data resident on the infected machines impossible. In its previous guise, Shamoon made machines unusable, but the potential existed to recover data from the crippled machines. This is not the case with the new version, which also contained lists of network attached computers to facilitate the spreading of the virus once it had infected a machine. A new component in Shamoon called the Spreader consults the list of computers and copies the wiping component to all devices on the list.
These new attacks also focused on companies involved in the gas and oil industry. Italian oil services enterprise Saipem had hundreds of servers located in the Middle East attacked. Other organizations in the United Arab Emirates and Saudi Arabia were also impacted in the same week.
Research into Protection Against the Shamoon Virus
The new variants of Shamoon are being disguised as legitimate software packages, according to bleepingcomputer.com. Recent variants contain expired digital certificates from Chinese technology company Baidu. The internal file names indicated that the files were associated with setting up a Baidu hotspot. It appears that the forces behind the malware are honing their delivery methods in the hopes of avoiding detection.
Data recovery experts are obviously interested in their ability to assist customers after they experience a data loss event. The destruction caused by the original Shamoon was confined to the MBR of the affected machine. Removing the hard drive and placing it in another computer would potentially lead to the recovery of its data. The current variant of the malware poses the further problem of deleted files.
The engineers at CleverFiles are conducting extensive research into the ability of their algorithms to successfully recover data that is deleted by infection with Shamoon. Their Disk Drill data recovery software can restore accidentally deleted files as well as data from formatted disks. Current research is focused on gaining the ability to recover data from machines that have been attacked by Shamoon.
Unfortunately, the presence of destructive malware is only likely to grow as time goes on. Protection from these devastating attacks needs to include detection to ward off the intrusion of the malware as well as tools to help with the recovery of damaged computers. Working in tandem, anti-virus and data recovery software may help our critical digital systems remain safe.