What is System Integrity Protection?
System Integrity Protection (SIP) is a new macOS security feature that Apple first unveiled in OS X 10.11 El Capitan. That happened to also be the last vision of Apple’s operating system named in the OS X fashion. Subsequent releases, which also feature SIP, used macOS instead and then refer to the actual version. Therefore, if you are running OS X El Capitan, macOS 10.12 Sierra, macOS 10.13 High Sierra or macOS 10.14 Mojave, you need to understand what SIP is and why Apple feels you need it on your computer.
System Integrity Protection is also known as “rootless” since it restricts the functionality of the root account on the operating system. Mac OS X is a Unix-like operating system and as such, allowed a root user access to the entire operating system. Root control lets the user overwrite or delete any system file or app, and can be extremely dangerous if not used with caution. Root permissions in the wrong hands can cause significant damage to your system. One of the factors that drove Apple to institute SIP is the threat posed by malware that could obtain unauthorized root permission on your system and take control of your computer.
SIP protects access to system locations and prevents your system from being compromised by malicious runtime attachments to system processes. It can have an impact on independently developed apps if they are not distributed through the Mac App Store. While Apple no doubt has only good intentions in restricting access to portions of your Mac’s operating system, some users may disagree and be concerned with the limitations enforce by SIP. Some analysts contend that Apple may be moving the macOS in the very closed direction of iOS, requiring a process similar to jailbreaking in order to install apps.
Key concepts that SIP enforces
#1 – Prevent writing to system locations
Only system processes that have been signed with Apple’s code signing identity can write to or modify files in certain system directories. They are:
/bin
/sbin
/usr
/system
Third-party developers can use /usr/local, /Applications, and[~] /Library as locations for their code.
#2 – Runtime protections
Processes are protected against modification and the kernel denies any attempt to attach to a protected process. At process initiation, the kernel verifies that the executable is either protected on disk or signed with special system entitlement. If neither is true then the executable is protected by the kernel.
#3 – Kernel Extensions
Kernel extensions, or kexts, now need to be signed with a Developer Id for Signing Kexts certificate and installed into the /Library/Extensions directory.
#4 – Other Ramifications of SIP
The familiar option that allows you to repair disk permissions has been removed from Disk Utility. Even as root user you cannot remove files like Chess.app and Mail.app. This also inhibits malware from tampering with these files.
Why is System Integrity Protection Important?
The security of your computer system is of critical importance to a vast majority of users. Your Mac may contain sensitive personal and financial information that could be extremely harmful if in the wrong hands. In most cases, more security is a good thing when discussing computers.
According to Apple, unrestricted root access was a major weakness of the operating system. It allows full control of a system to be gained by a malware attack by taking advantage of a single vulnerability or obtaining one critical password. The company sees the enforcement of SIP as a vital component in providing their systems with the highest level of security possible.
Configuring SIP Settings
Security Integrity Protection applies its setting to all installations of macOS across an entire machine. This is accomplished by storing the configuration in NVRAM instead of the file system. Another safety feature is the inability to programmatically set the startup disk. This would allow SIP to be subverted with security configuration from another operating system.
To determine if SIP is enabled on your system open up a Terminal window and enter the command:
csrutil status
Since the configuration is stored in NVRAM it can only be modified in the machine’s recovery environment. If you need to totally disable SIP for a valid reason, and you should indeed have a valid reason to do this, here’s what to do.
- Boot to Recovery OS. You can do this by holding down the Command and R keys when restarting your computer.
- Start the Terminal application.
- Enter this command to disable SIP:
csrutil disable
When you want to turn it back on, follow these steps.
- Boot to Recovery OS. You can do this by holding down the Command and R keys when restarting your computer.
- Start the Terminal application.
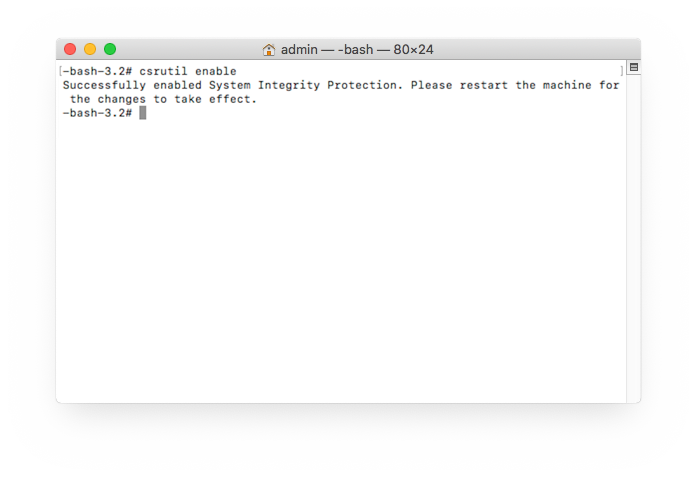
- Enter this command to disable SIP:
csrutil enable
In general, you should not have to take these steps and should rely on Security Integrity Protection to keep your machine operating safely. Let’s look at an example when you will have to disable SIP in order to get some work done on your system.
Disk Drill and SIP
While most users will not need the level of access that SIP denies them, there are situations where applications will not operate correctly unless SIP is disabled. Disk Drill data recovery software is an example of a utility that will not be able to run its magic on your system drive with SIP enabled.
When attempting data recovery on your startup disk, Disk Drill requires read-only access. Under normal circumstances, this is not allowed on your post-High-Sierra macOS machine. In order to use Disk Drill for your startup disk, you will need to partially disable SIP on your Mac. You can find full details on how to manage SIP in the Disk Drill Knowledge Base. Our recent research also confirms that some external storage devices used for Time Machine backups may also fall under SIP. Luckily, it’s an easy fix.
Temporarily disabling SIP will not lead to any negative impact on your system and is necessary in order to harness the power of Disk Drill to recover data on your startup disk. When you’re done, make sure you enable SIP again to keep your newly recovered data, as well as your complete system, safe and secure.